
th10 hybrid attack strategy | miner hog hybrid attack th10 | best th10 attack strategy 2020 - YouTube
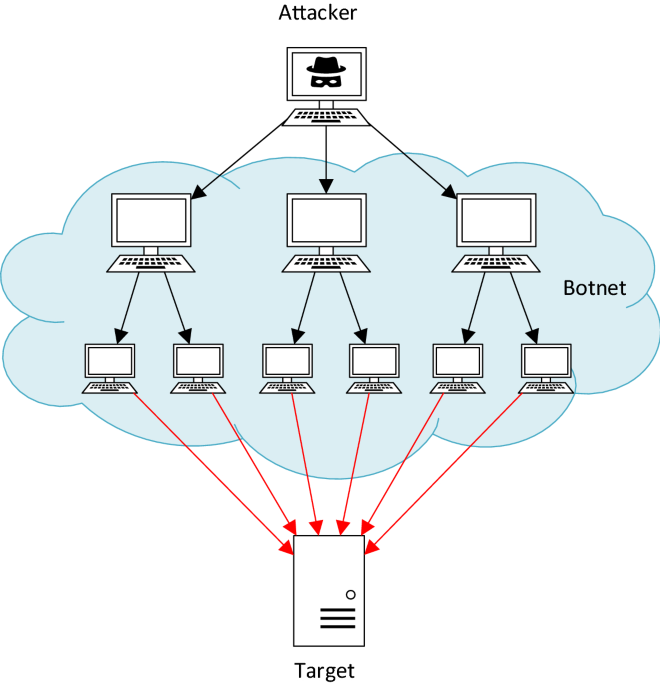
A hybrid machine learning approach for detecting unprecedented DDoS attacks | The Journal of Supercomputing
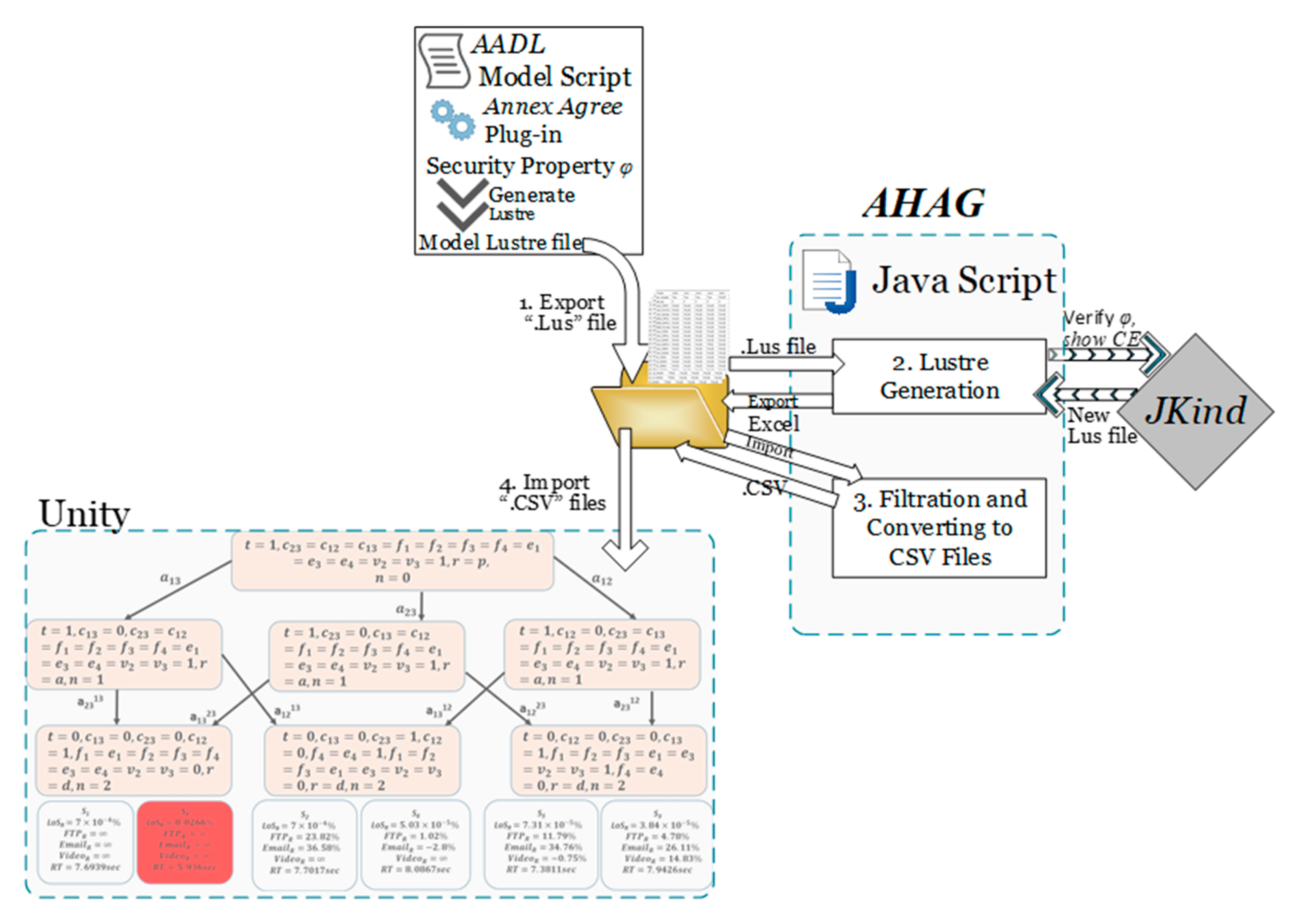
Processes | Free Full-Text | Automatic Hybrid Attack Graph (AHAG) Generation for Complex Engineering Systems
![PDF] Automatic Hybrid Attack Graph (AHAG) Generation for Complex Engineering Systems | Semantic Scholar PDF] Automatic Hybrid Attack Graph (AHAG) Generation for Complex Engineering Systems | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/20ef3f5cd0af83b1e3957d17a13c4bb31183d70e/5-Table1-1.png)

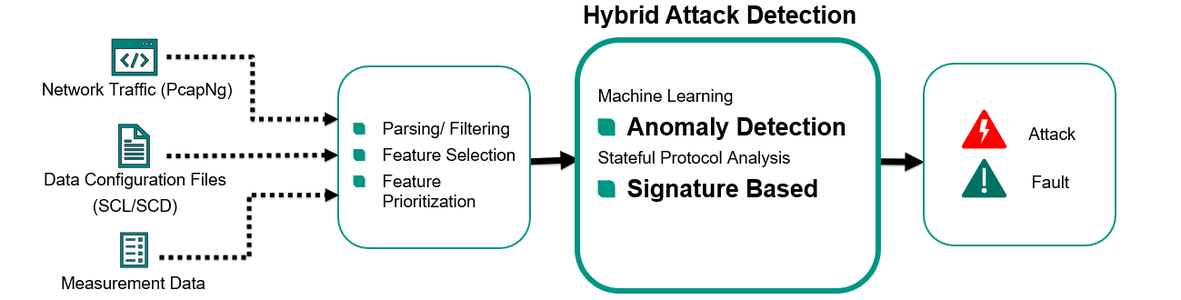







![ALERT] There Is A New Hybrid Cyber Attack On Banks And Credit Unions In The Wild ALERT] There Is A New Hybrid Cyber Attack On Banks And Credit Unions In The Wild](https://blog.knowbe4.com/hubfs/hybrid_attack.png)


